In order to understand Amazon s3 and glacier server side security, we need to understand how Amazon store our data with both of the services and what option we have to encrypt data.
Amazon S3 Server-Side Encryption(SSE):
- Amazon S3 encrypts at the object level as it writes data to disk in its data centers
- S3 decrypts the data on retrieval as long as a user or service has permissions to retrieve it
- There are three options for dealing with encryption keys:
- Amazon S3-Managed Keys (SSE-S3)
- AWS KMS-Managed (SSE-KMS)
- Customer-Provided Keys (SSE-C)
Amazon S3-Managed Keys (SSE-S3):
- Each Object is encrypted with a unique key
- Those unique keys are themselves encrypted with a master key
- The master key is regularly rotated
- Amazon S3 uses the 256-bit Advanced Encryption Standard (AES-256), this is one of the strongest block size available.
Eg: How to encrypt data which is already existing in the file.
Assume there is one file in S3 “user-secret.txt” and I want it to encrypt, So here we go:
- Right-click on the file and go to properties
- Explore the “Details” tab
- Look at the “server-side encryption” and select AWS-256 and save it.
This will automatically encrypt this file on the server-side in Amazon DataCenters. So, now the file is encrypted. We can view it in the same way/download it because we have IAM permission and Amazon decrypt automatically.
Amazon S3-Managed Keys (SSE-S3) – API:
- Encrypting data with this method via the REST API requires this header:
- x-amz-server-side-encryption
- AWS SDKs provide wrappers which automate this step-through method
For Eg: If you want to upload objects with the “put” operation we can specify the header and the object will be encrypted by an Amazon S3 as it is written to disk.
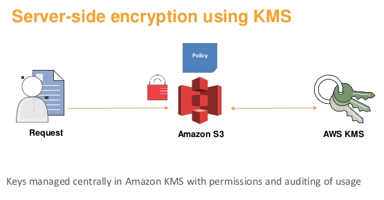
AWS KMS-Managed (SSE-KMS)
- AWS KMS provides a central location for key management
- KMS uses Customer Master Keys (CMKs) to encrypt and decrypt S3 objects
- It integrates with Amazon S3 and IAM in order to provide complete control over how keys are used
- It also provides key usage auditing, rotation and the ability to disable keys
- Please Note:
- Encryption keys can be created and managed by the customer, or default service keys can be used instead
- Data keys used to encrypt S3 data is also encrypted and stored with the data itself
AWS KMS-Managed (SSE-KMS) – API
- Encrypting objects with AWS KMS requires the use of this header:
- X-amz-server-side-encryption with value aws:kms
- There is also another header for encryption:
- X-amz-server-side-encryption-aws-kms-key-id
- This header gives the ability to specify the ID of the AWS KMS master encryption key to be used for an object (otherwise the default key is used)
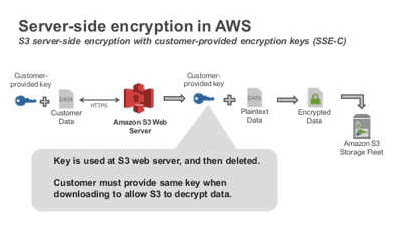
Customer-Provided Keys (SEE-C)
- This method gives customers complete control over their encryption keys
- Amazon S3 still manages the encryption and decryption process but customers provide the keys
- S3 does not store the encryption key provided
- Instead, it stores a randomly salted HMAC value of the encryption key
- This allows S3 to validate requests
- If the customer loses the key, they lose the object
- Decrypting objects requires the same encryption key to be provided with the request
- This method requires HTTPS requests to encrypt the key in-transit
- The customer is responsible for tracking which key is used to encrypt which object because S3 does not
- The Amazon Console cannot be used to upload or modify objects with this method. The API or SDKs must be used.
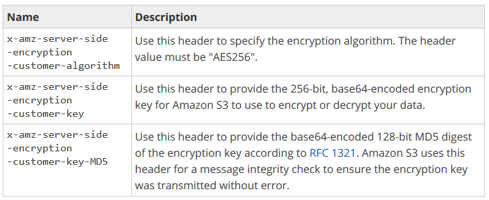
- Encryption key information must be provided with these headers as mention in below images:
Amazon Glacier Encryption:
- All data stored in Glacier is encrypted and key management is managed for the customer
- Encryption uses AES-256
- Customers wanting to manage their own keys can encrypt data before uploading it, decrypt data upon retrieval
End of the article, Amazon S3 and Glacier Server Side Security.
Thanks for reading this article, you’ll also like:
AWS Value and Widest Service offering
Amazon EC2 M5 vs M4 Instance Comparison
When to switch to a bigger RDS instance
Amazon Web Services Interview Questions